Platform
Platform
Everything you need to run a secure global network—in a single system.
CommandLink ITSM
How we scale your IT resources
Integrations
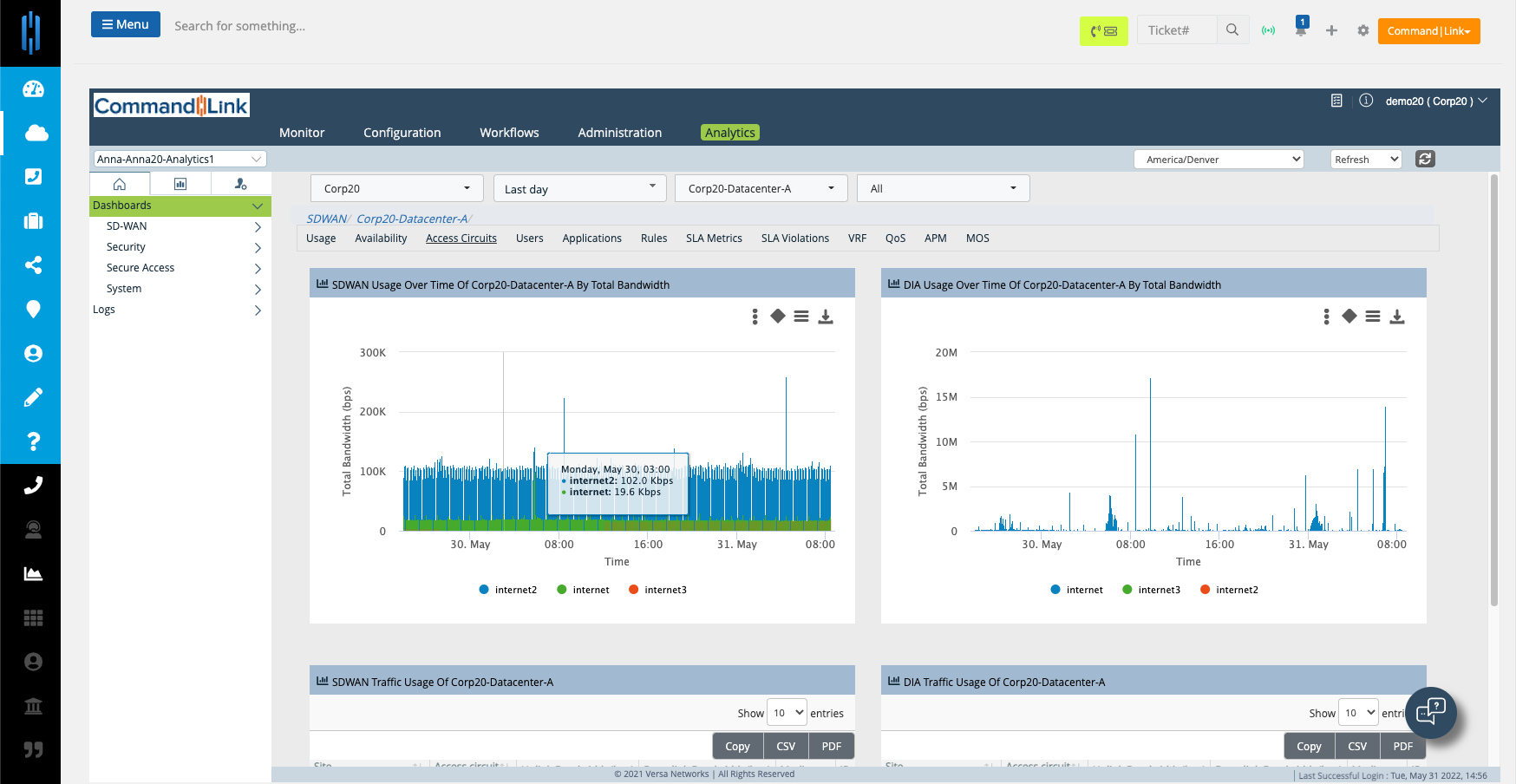
Full analytics and management integrations
Cloud Network
The most reliable cloud network
Strategy + Design
Powerful outcomes
Deployment
The ultimate deployment strategy
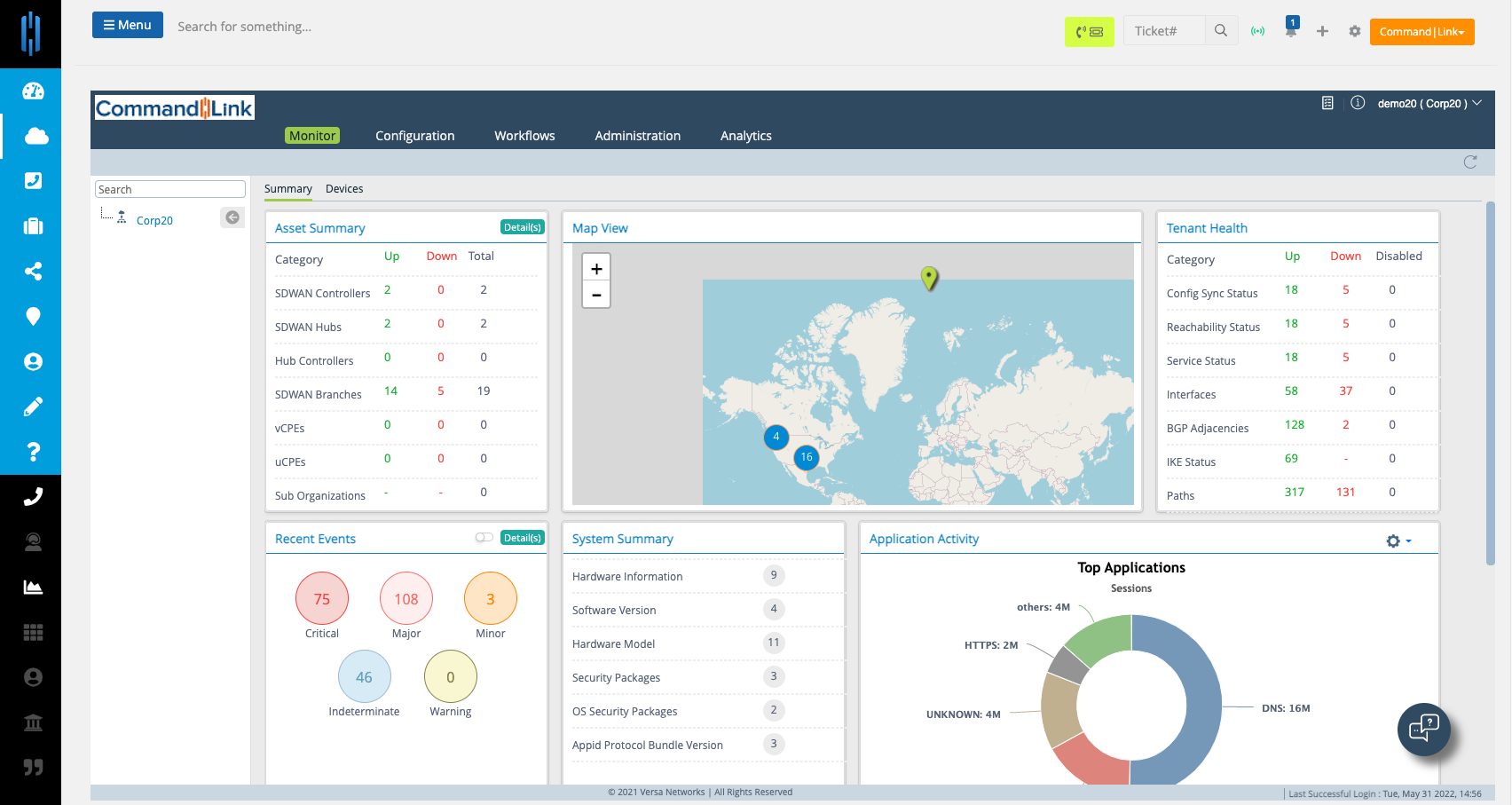
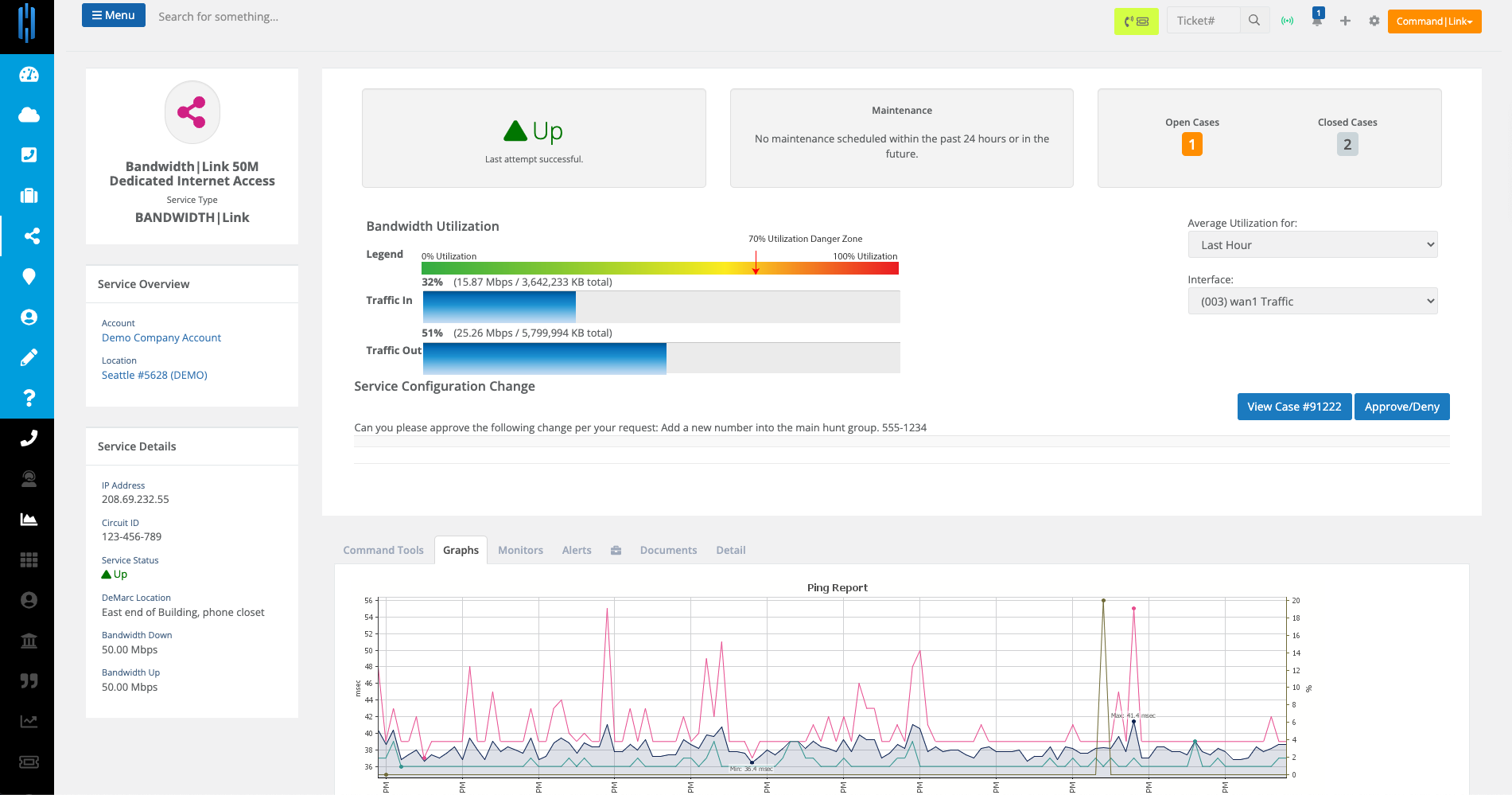
Monitoring & Alerts
Get full scale monitoring support
Solutions
Solutions
Learn how our solutions were designed to help you scale your IT resources
Company
CommandLink
Let's talk about how we can help you!
Partners