Platform
Platform
Everything you need to run a secure global network—in a single system.
Solutions
Solutions
Learn how our solutions were designed to help you scale your IT resources
Company
CommandLink
Let's talk about how we can help you!
Partners
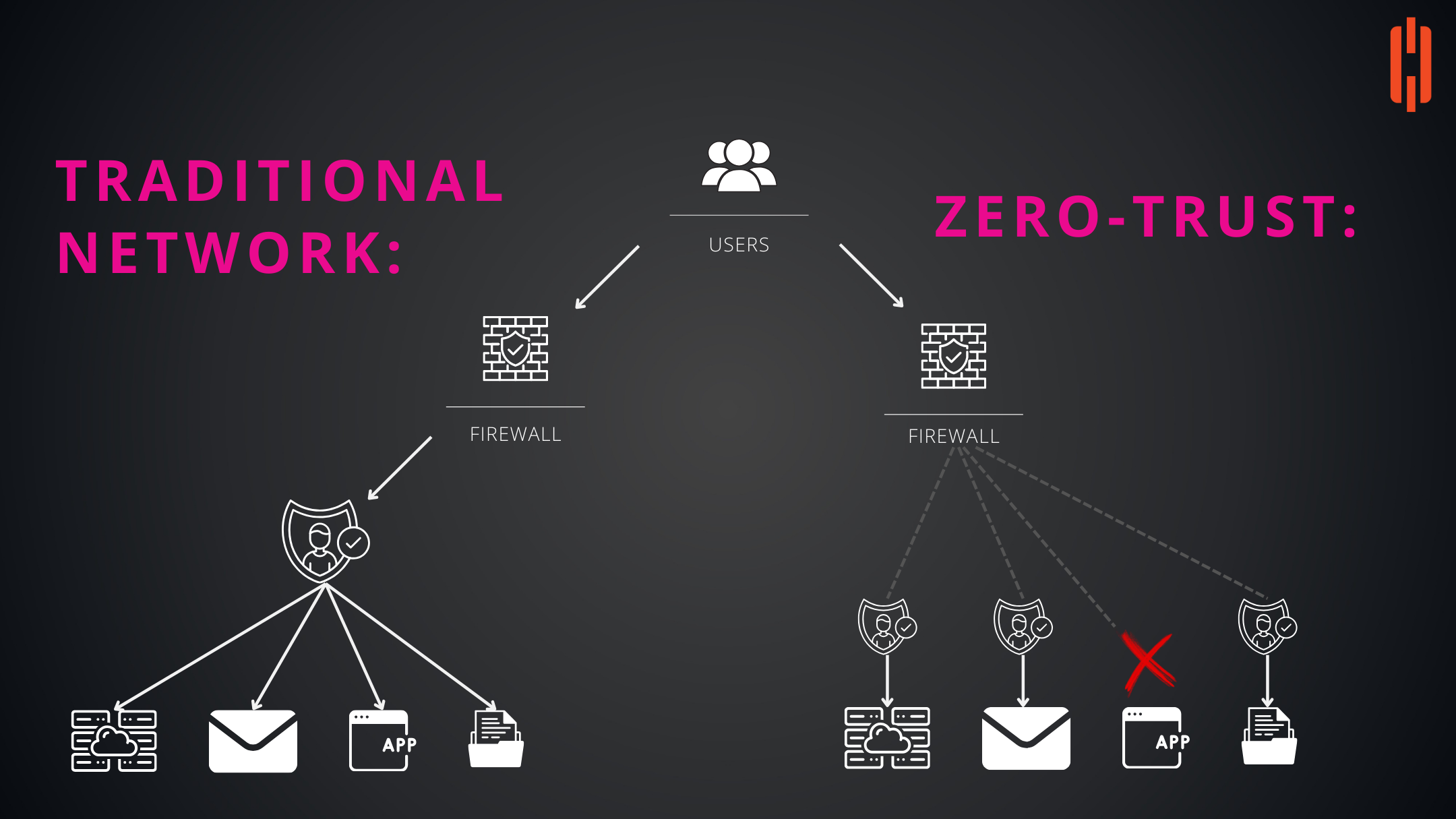
Traditional Network Security The traditional network security model is depicted as a castle-and-moat approach. It relies on strong perimeter defenses like firewalls to protect resources within the network. Once inside the network—akin to being inside the castle walls—users and systems are generally trusted by default. The graphic illustrates users having unfettered access to various applications and services, represented by the email, cloud, and printer icons, once they are past the firewall.
This model worked well when organizations operated on-premises and had clear network boundaries. However, with the advent of cloud computing, mobile workforces, and BYOD (Bring Your Own Device) policies, this trust-based model has shown vulnerabilities. It assumes that threats come primarily from outside the network perimeter, but this is no longer the case in the current digital landscape.
Zero Trust Architecture Zero Trust is a strategic cybersecurity paradigm that eliminates the concept of trust from an organization’s network architecture. Rooted in the principle of "never trust, always verify," Zero Trust is designed to protect modern digital environments by leveraging network segmentation, preventing lateral movement, providing Layer 7 threat prevention, and simplifying granular user-access control.
The graphic showcases the Zero Trust approach, where every access request is thoroughly vetted, regardless of its origin. It highlights the dynamic nature of this security model with dashed lines indicating the conditional and scrutinized access to network resources. Notably, one application is marked with a red cross, signifying denied access under Zero Trust policies. This represents the stringent access controls and continuous verification of all devices and users, irrespective of their location—inside or outside the organization’s network.
The Zero Trust Model: Core Principles
Implementing Zero Trust To implement a Zero Trust architecture, an organization must evaluate and understand the flow of data and how users, both internal and external, interact with the system. Tools such as multi-factor authentication, identity and access management (IAM), orchestration, analytics, encryption, scoring and file system permissions play a significant role.
The transition from a Traditional Network to a Zero Trust model is not just a shift in technology but a fundamental change in the organization’s approach to cybersecurity. As the graphic by Command Link indicates, the perimeter-based model of the past is giving way to a more robust, flexible, and secure approach that can adapt to the complexities of modern IT environments. This move is essential to protect against both external threats and threats from within, ensuring the integrity and resilience of an organization's data and systems.
Zero Trust is more than a security model—it is a journey that requires a change in mindset. Organizations must commit to an ongoing process of evaluating their security stance, understanding that the network perimeter is no longer a singular line of defense but a multi-faceted, strategic framework designed to secure a digital ecosystem that is constantly evolving.