Platform
Platform
Everything you need to run a secure global network—in a single system.
Solutions
Solutions
Learn how our solutions were designed to help you scale your IT resources
Company
CommandLink
Let's talk about how we can help you!
Partners
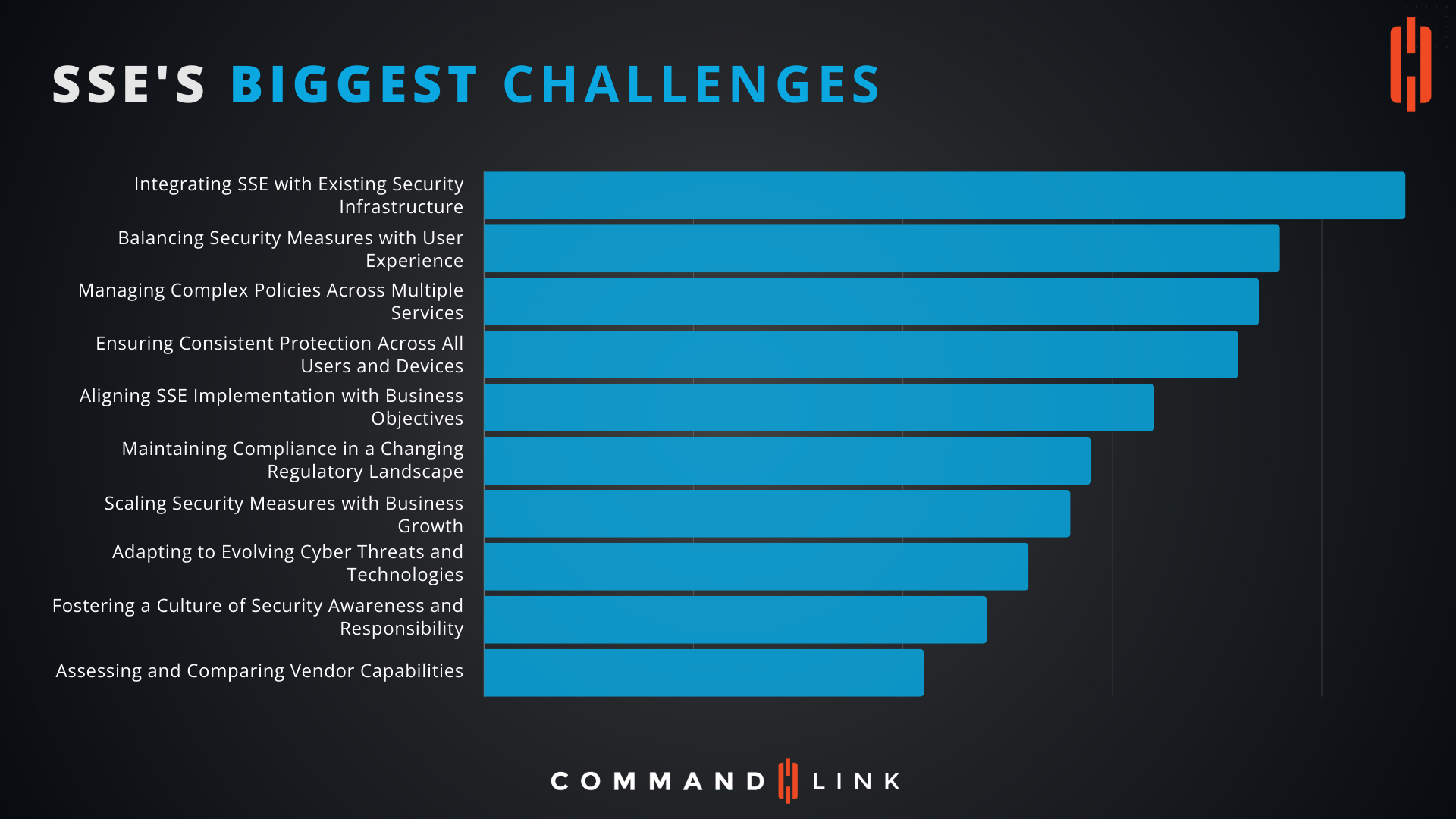
Overcoming SSE's Biggest Challenges: A Comprehensive Guide
Secure Service Edge (SSE) is a critical component in the modern security architecture, especially as businesses increasingly adopt cloud-based services and remote work models. However, implementing and managing SSE comes with its own set of challenges. This article delves into the top challenges organizations face when integrating SSE into their security framework and offers insights into how to overcome them.
How Can We Integrate SSE with Existing Security Infrastructure?
One of the most significant challenges in adopting SSE is ensuring seamless integration with the existing security infrastructure. Organizations often have a variety of security tools and platforms already in place, and integrating SSE into this complex environment can be daunting. The key to overcoming this challenge is careful planning and a phased approach to implementation. Businesses should start by conducting a thorough assessment of their current security landscape, identifying potential integration points, and gradually introducing SSE solutions that complement and enhance existing security measures.
How Do We Balance Security Measures with User Experience?
Balancing robust security with a smooth user experience is a perennial challenge in cybersecurity. SSE, by design, introduces additional security layers, which can sometimes lead to latency or a more complex user interface. To address this, organizations should focus on optimizing network performance and ensuring that security measures are as transparent as possible to end users. Regular feedback loops with users can also help identify pain points and areas where the security experience can be improved without compromising protection.
How Can We Manage Complex Policies Across Multiple Services?
As organizations expand their use of cloud services, managing security policies across these platforms becomes increasingly complex. SSE provides a unified framework for enforcing security policies, but managing these policies effectively across multiple services can be challenging. To mitigate this, businesses should invest in centralized policy management tools that offer visibility and control over security configurations across all services. Automation and policy templates can also reduce the burden of manual configuration and ensure consistency across the board.
How Can We Ensure Consistent Protection Across All Users and Devices?
With the rise of remote work and Bring Your Own Device (BYOD) policies, ensuring consistent protection for all users and devices is more critical than ever. SSE's ability to enforce security at the network edge is crucial, but organizations must also ensure that these protections extend to all endpoints, regardless of location or device type. Implementing endpoint detection and response (EDR) solutions in tandem with SSE can provide comprehensive protection across the entire network and all connected devices.
How Can We Align SSE Implementation with Business Objectives?
Security strategies must align with broader business objectives to deliver real value. However, aligning SSE implementation with these goals can be challenging, particularly when business needs evolve rapidly. Organizations should involve business leaders in the planning and execution of SSE initiatives, ensuring that security measures support business outcomes rather than hinder them. This alignment can be achieved through regular communication and by tying SSE metrics to key business performance indicators.
How Do We Maintain Compliance in a Changing Regulatory Landscape?
Regulatory compliance is a moving target, with new laws and standards emerging regularly. Keeping up with these changes while implementing SSE can be overwhelming. To stay compliant, organizations should adopt a proactive approach, regularly reviewing and updating their security policies to meet current regulations. SSE platforms that offer built-in compliance reporting and monitoring tools can also ease the burden of maintaining compliance across diverse environments.
How Can We Scale Security Measures with Business Growth?
As businesses grow, so do their security needs. Scaling SSE solutions to match this growth without compromising security is a significant challenge. The key to scaling effectively is adopting a modular approach to SSE, where components can be added or upgraded as needed. Cloud-native SSE solutions are particularly well-suited to scaling, as they can flexibly adjust to changes in demand and capacity. Regular assessments of security posture relative to business growth can also help identify when and where scaling is necessary.
How Can We Adapt to Evolving Cyber Threats and Technologies?
Cyber threats are constantly evolving, and staying ahead of these threats requires continuous adaptation and innovation. SSE provides a strong foundation for security, but organizations must remain vigilant and proactive in adapting their security strategies to new and emerging threats. This involves staying informed about the latest threat intelligence, regularly updating security technologies, and fostering a culture of continuous improvement in security practices.
How Can We Foster a Culture of Security Awareness and Responsibility?
Even the most advanced security technologies are ineffective if users are not aware of or do not follow security best practices. Fostering a culture of security awareness and responsibility is essential for the success of SSE initiatives. This can be achieved through regular training, clear communication of security policies, and by encouraging a sense of shared responsibility for security throughout the organization. When employees understand the importance of security and their role in maintaining it, they are more likely to follow protocols and report suspicious activities.
How Can We Assess and Compare Vendor Capabilities?
Selecting the right SSE vendor is a critical decision that can significantly impact the effectiveness of your security strategy. However, assessing and comparing vendor capabilities can be challenging, particularly given the wide range of options available. Organizations should approach vendor selection with a clear set of criteria based on their specific security needs and objectives. This might include evaluating vendors' track records, their ability to integrate with existing systems, the flexibility and scalability of their solutions, and their commitment to ongoing support and innovation.
Implementing SSE is a complex but essential step for organizations looking to enhance their security posture in today's digital landscape. By addressing these challenges—integrating with existing infrastructure, balancing security with user experience, managing complex policies, ensuring consistent protection, aligning with business objectives, maintaining compliance, scaling with growth, adapting to evolving threats, fostering security awareness, and selecting the right vendors—businesses can successfully navigate the complexities of SSE and build a more secure and resilient organization.