Platform
Platform
Everything you need to run a secure global network—in a single system.
Solutions
Solutions
Learn how our solutions were designed to help you scale your IT resources
Company
CommandLink
Let's talk about how we can help you!
Partners
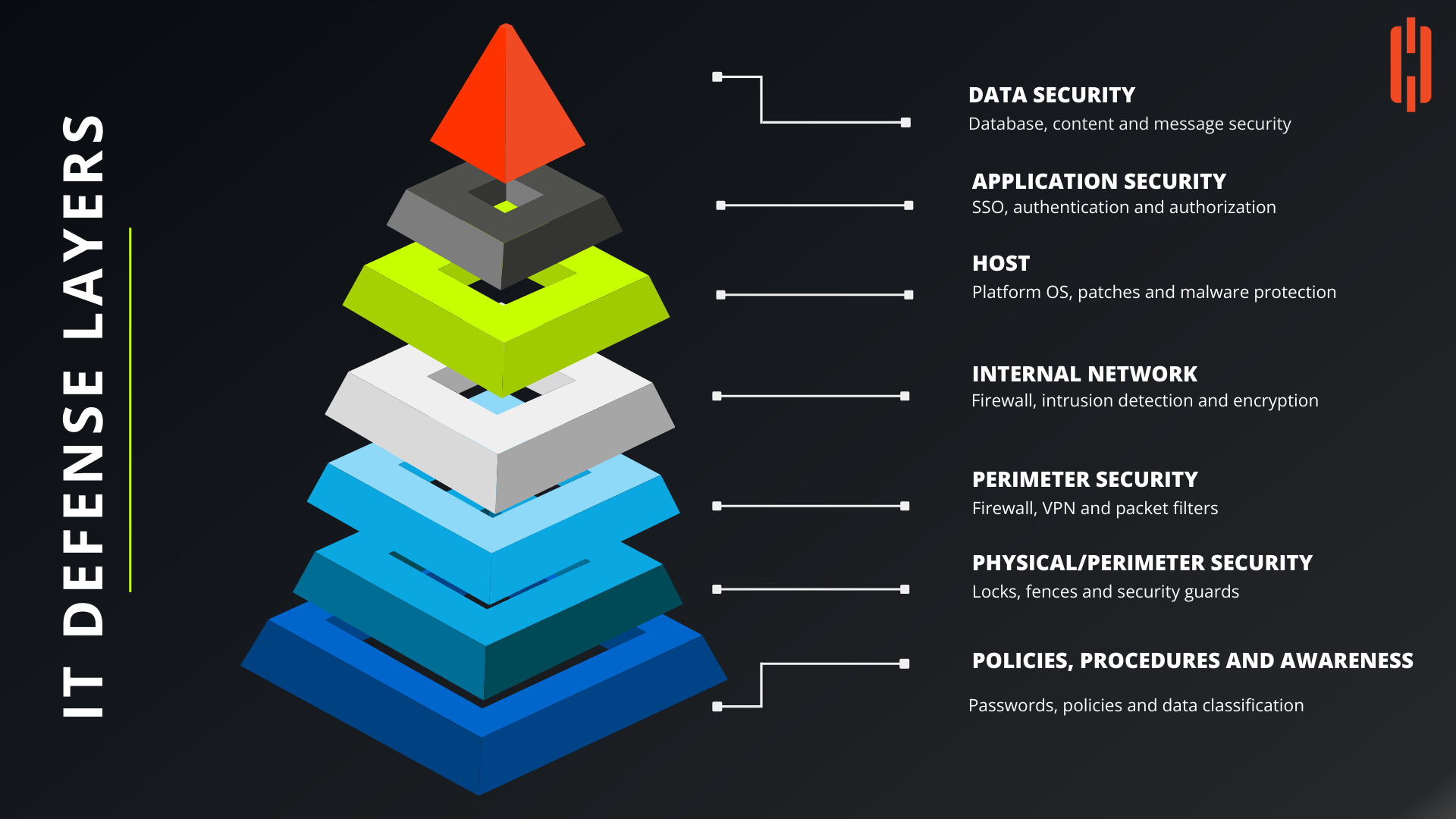
How Can IT Defense Layers Enhance Your Organization's Security?
In the rapidly evolving landscape of cybersecurity, it is crucial for organizations to implement robust defense strategies that can withstand various threats. One such strategy is the implementation of IT defense layers, which provide a multi-faceted approach to security. But how exactly do these layers work, and how can they be effectively utilized to enhance your organization's security?
What Is the Role of Data Security in IT Defense Layers?
At the top of the IT defense hierarchy is data security, which focuses on protecting the most critical assets of any organization: its data. This layer encompasses database security, content security, and message security, ensuring that sensitive information is protected from unauthorized access and breaches. By implementing strong encryption and access control measures, organizations can safeguard their data against potential cyber threats.
Why Is Application Security Important for Your Organization?
Application security is the second layer of defense, emphasizing the protection of software applications used within the organization. This includes implementing Single Sign-On (SSO) systems, as well as authentication and authorization protocols. By securing applications at this level, organizations can prevent unauthorized users from gaining access to critical systems, thus reducing the risk of security breaches.
How Does Host Security Contribute to Overall IT Defense?
Host security, which focuses on securing the platform's operating system, patches, and malware protection, is another vital layer in the IT defense strategy. Ensuring that all systems are regularly updated with the latest security patches and are equipped with robust malware protection can prevent vulnerabilities from being exploited by attackers.
What Is the Significance of Internal Network Security?
The internal network layer is responsible for safeguarding the organization's internal communications and data transfer processes. This includes implementing firewalls, intrusion detection systems, and encryption protocols to monitor and protect internal network traffic. By securing this layer, organizations can detect and respond to potential threats before they infiltrate deeper into the system.
How Do Perimeter Security Measures Protect Your Organization?
Perimeter security serves as the first line of defense against external threats. This layer includes firewalls, Virtual Private Networks (VPNs), and packet filters that help monitor and control incoming and outgoing network traffic. By establishing a secure perimeter, organizations can prevent unauthorized access and reduce the risk of external attacks.
Why Is Physical/Perimeter Security Still Relevant in the Digital Age?
Even in the digital era, physical and perimeter security measures remain essential. This layer includes physical barriers such as locks, fences, and security guards, which protect the physical infrastructure of an organization. These measures ensure that only authorized personnel have access to sensitive areas, thereby reducing the risk of physical breaches.
What Role Do Policies, Procedures, and Awareness Play in IT Defense?
At the foundation of IT defense layers are the policies, procedures, and awareness programs that guide the organization’s overall security strategy. This layer involves implementing strong password policies, data classification guidelines, and ongoing security awareness training for employees. By fostering a culture of security within the organization, these foundational elements help reinforce the effectiveness of all other defense layers.