Platform
Platform
Everything you need to run a secure global network—in a single system.
Solutions
Solutions
Learn how our solutions were designed to help you scale your IT resources
Company
CommandLink
Let's talk about how we can help you!
Partners
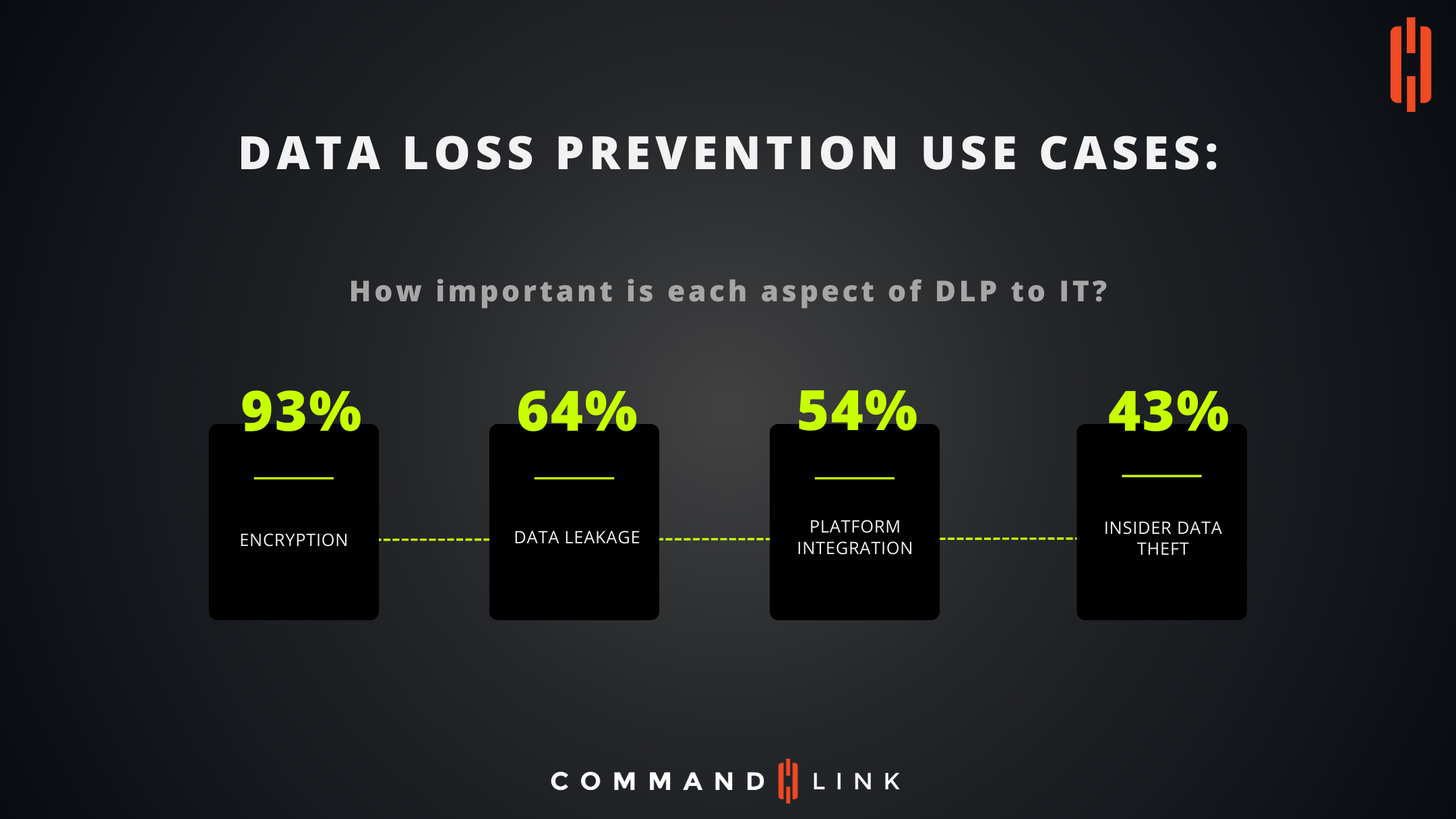
Encryption: The Paramount Defense Mechanism
93%: The Critical Role of Encryption Encryption emerges as the paramount tool in the DLP arsenal, with a staggering 93% of IT professionals deeming it important. Encryption transforms sensitive information into a nearly unbreakable code, guarding data against unauthorized access, both at rest and in transit. Its overwhelming importance underscores the necessity of robust encryption protocols to protect against external threats and potential internal vulnerabilities.
Data Leakage: Vigilance Against Unintentional Exposure
64%: Preventing Data Leakage Another major aspect of DLP, as highlighted by 64% of IT professionals, is the prevention of data leakage. Data leakage refers to the unauthorized transmission of data from within an organization to an external destination or recipient. This can occur through various means, including email, cloud storage, and mobile data transfer. Organizations are increasingly vigilant about preventing such leaks, as they can lead to significant financial and reputational damage.
Platform Integration: Seamless DLP Operations
54%: Emphasizing Platform Integration With 54% considering it important, platform integration signifies the seamless incorporation of DLP solutions within the existing IT infrastructure. DLP tools must be compatible with various platforms and devices to provide comprehensive protection. Integration is key to operational efficiency and ensures that DLP measures do not disrupt business processes while still providing effective data protection.
Insider Data Theft: An Ever-Present Threat
43%: Mitigating Insider Data Theft While lower on the priority list with 43%, addressing insider data theft is still a crucial concern. Insider threats can be particularly difficult to manage as they involve users who have legitimate access to the company's data. These threats can range from unintentional data exposure by employees to deliberate theft or sabotage. A multi-layered approach, including user behavior analytics and strict access controls, is vital to combat this issue.
Strategies for Effective Data Loss Prevention
Given the highlighted statistics, implementing a comprehensive DLP strategy should be a multifaceted effort:
1. Strengthen Encryption Practices Investing in strong encryption practices is non-negotiable. Organizations should use advanced encryption standards and ensure that encryption keys are securely managed.
2. Leverage Data Leakage Solutions Utilize advanced DLP solutions capable of monitoring and controlling data flow. These solutions should cover both physical and virtual data transfers.
3. Enhance Platform Integration Choose DLP solutions that integrate well with the existing IT landscape. Seamless integration promotes user adoption and simplifies monitoring.
4. Address Insider Threats Proactively Create a culture of security awareness and implement the principle of least privilege. Regularly monitor and audit data access to identify potential insider threats early.
The statistics from Command Link's infographic reflect a clear recognition of the critical elements within DLP. Encryption, data leakage prevention, platform integration, and insider threat mitigation are all essential components that IT departments must address to protect organizational data. By prioritizing these aspects, organizations can establish a robust defense against the diverse range of data loss risks they face in today's digital environment.